Over 70 million new, compromised email addresses at haveibeenpwned.
With these free online tools, you can immediately check whether your email address has been leaked on the internet and is associated with stolen data. One of the two tools, haveibeenpwned, has just received a huge update with over 70 million new compromised email addresses.
haveibeenpwned by Troy Hunt
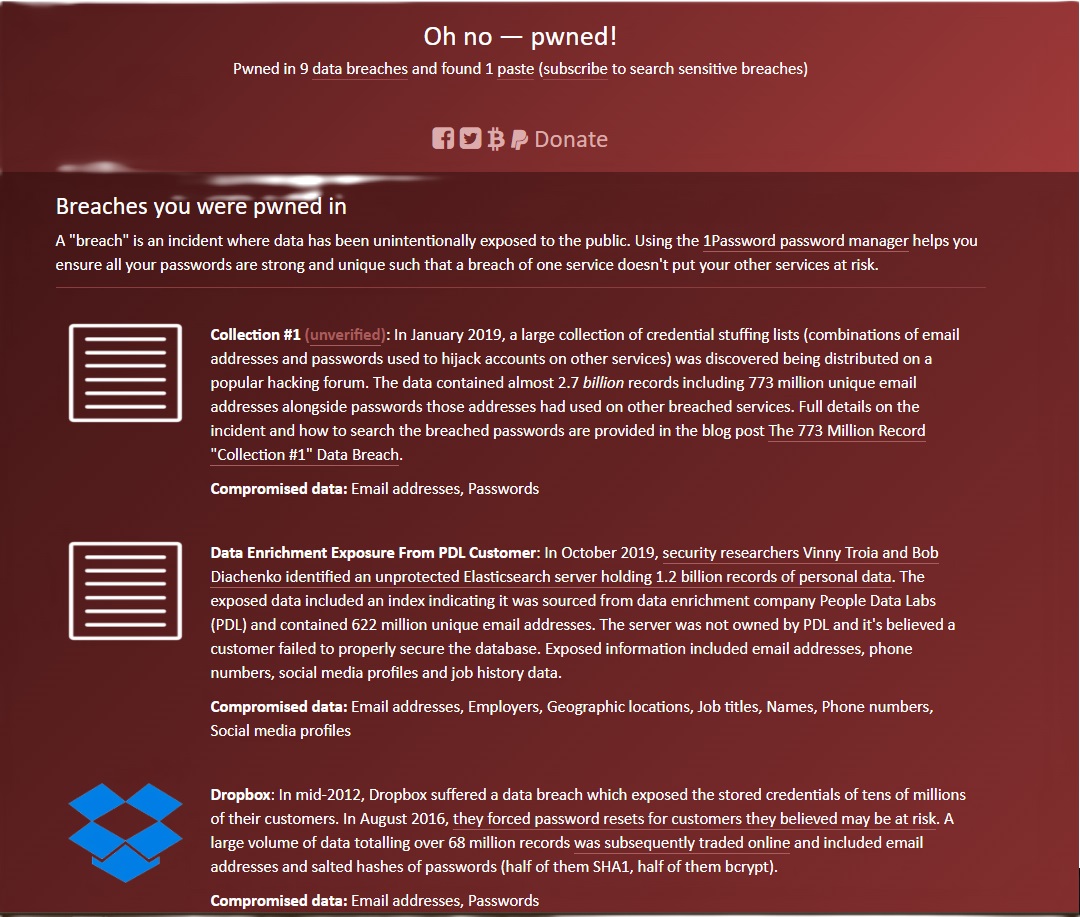
On haveibeenpwned you can have your email address checked by the operator Troy Hunt to see whether it appears on the internet in connection with leaked data. The page shows you the result of the check immediately. See the following screenshot:
Foundry
The result gives tips on how to improve the security of the affected mail account and explains in which breaches your mail password was discovered. The site also offers the option of checking telephone numbers to see whether they appear in breaches. You can also search for stolen passwords. You can also be notified automatically if your email address stored with haveibeenpwned appears in a breach.
Important: Even if your email address does not appear in a data leak, this does not mean that it has not already been hacked or is not easy to hack — for example, because of a weak password. On the other hand, it does not necessarily mean that your email address is already being misused if it is included in a breach.
Tip: How to avoid email stalking and protect your privacy
It is theoretically true that haveibeenpwned can be misused under certain circumstances, by allowing anyone to enter your email address and potentially discover which cloud services you have registered with using that address (e.g., Dropbox in the image above). However, users who log in to potentially suspicious online services such as porn portals or online sex contact platforms with their professional or primary and generally known email address are acting extremely carelessly. For such purposes, you should create an additional, well-disguised email address whose name cannot be used to deduce your own identity.
HPI Identity Leak Checker
The HPI Identity Leak Checkerk from the Hasso Plattner Institute for Digital Engineering is another free online tool that you can use to check your email address to see whether it appears in breaches. Here, however, the result of the check is not displayed directly on the HPI Identity Leak Checker website, but instead the HPI Identity Leak Checker sends an email with the check result to the checked email address, see screenshot:
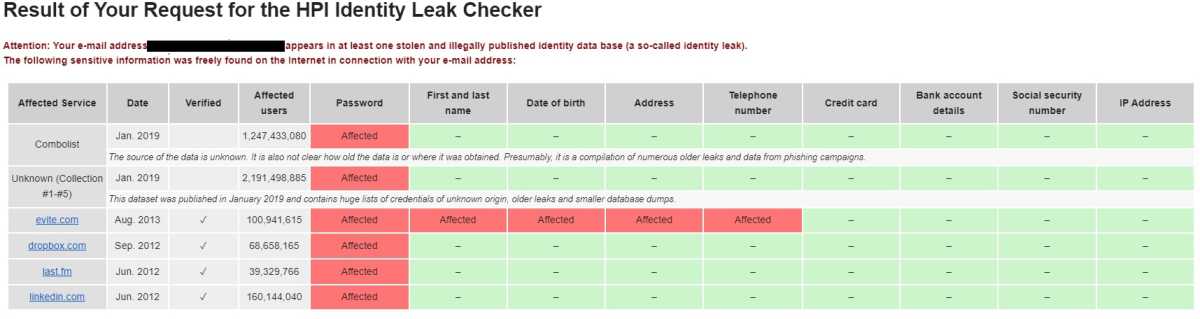
This means that HPI Identity Leak Checker cannot be used for stalking as with haveibeenpwned.
It is operated by the Hasso Plattner Institute (HPI) at the University of Potsdam. You can find details on how it works in the FAQ. Important: “The Identity Leak Checker only provides information on whether your password was found in a leak. The Leak Checker says nothing about whether this password still works for the affected user account. As your password can still be found in the corresponding leak, the website will continue to issue a warning.”
Identity Leak Checker of the University of Bonn
The University of Bonn also offers a leak checker. It works in exactly the same way as the HPI’s: You enter the email address to be checked and the analysis is then sent to the email address you entered. This also prevents stalking or spying attempts, as is theoretically possible with haveibeenpwned.
The Bonn Leak Checker was developed as part of the EIDI project, which is subsidized by the German government.
How to react correctly
If the tools mentioned above show you that your email address appears in data leaks/breaches, you should change your password immediately. If you have used the same password that you use for your email account for other services, you should also change this password there.
Very important: Install two-factor authentication if this is supported for your email account.
It’s also highly recommended that you use a password manager to create and save unique, secure passwords for all the sites and services you use. See our guide to the best password managers for suggestions.
Trending for you

Where do the stolen email addresses come from?
Most stolen email addresses originate from attacks on company servers that run services with which you have registered your email address. For example, cyber criminals stole the data of several hundred thousand customers of the Hessian energy supplier Entega. These data treasures are then offered for sale by the thieves in internet forums or on the darknet. Other major data thefts at company level include, for example:
You are powerless against such data leaks, which are caused by stealing server data; you cannot prevent them. But you can take measures to minimize the harms.




