These tweaks will make your router more secure.
Network security sounds like something that would concern an IT manager at a big company, but even ordinary home users have good reasons not to leave their small home networks to the wind. It’s about stopping hackers and malware from getting in from the outside, but it’s also about stopping unauthorized people from getting into and snooping around your connected devices–not to mention giving all those devices the best possible protection as they browse the internet.
In this guide, I’ll go through different aspects of network security and show you what you can do to increase your privacy and reduce the risk of hacks and malware, without making your life more complicated.
Securing your router
In most homes, the router is both the central hub of the local network and the gateway between the network and the vast, wild internet. All traffic between connected devices and the internet or between two connected devices passes through the router.
This means that the most important thing for a secure home network is a secure router, which neither lets unauthorized people in through weak passwords nor can be taken over by hackers or malware.
Strong passwords
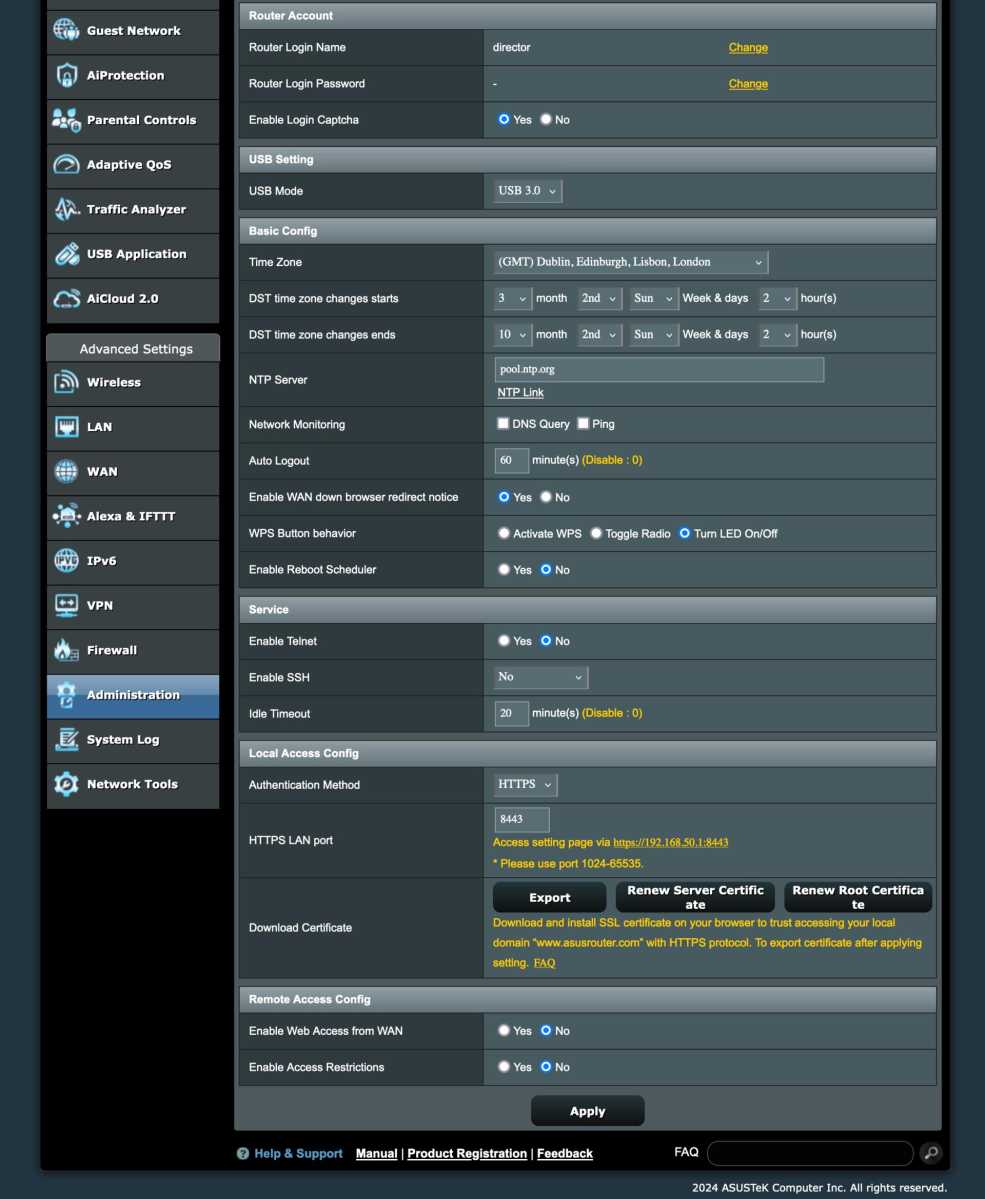
Start by choosing a strong, unique password for your router’s admin interface. If possible, change the username on your router as well. If a vulnerability is discovered in the router that makes it easier to guess the right password, a unique username can still put an end to automated login attempts.
Foundry
Enable https for the admin interface
If not already enabled, you should switch on https (encrypted connection) in the router settings. The setting for it is usually in the same place as the password. Without an encrypted connection, an unauthorized user on the local network can easily intercept your password and take control of the router.
Change your Wi-Fi name and password
Most routers come from the factory with a randomly chosen wireless network name and an equally random password. This can lull you into a false sense of security, thinking that’s enough. This is a mistake, as it has been shown many times over the years that these are not as random as they seem, and are easy to circumvent. The random network names (also called SSID) also reveal the manufacturer of your router, making it easier to target it with attacks.
So switch to a unique network name (it also makes it easier to recognize your network if your neighbors have routers from the same manufacturer) and a long, secure password. I strongly recommend a password consisting of common, randomly chosen words. It’s much easier to type in by hand than a string of characters.
Select wpa2
For connection security to the wireless network, it’s often possible to choose between different versions of the wpa protocol. Some routers are still pre-set to use wpa1 (usually just called wpa), but this is an outdated standard that is not completely secure. The vast majority of devices today support wpa2 or wpa3, so I recommend starting with wpa3 only. If you then find that any device in your home cannot connect to the network, you can go back to the router settings and change it to wpa2/wpa3. If that option is not available, you can choose wpa2 only.
You may also want to activate a function called protected management frames if this option is available.
Foundry
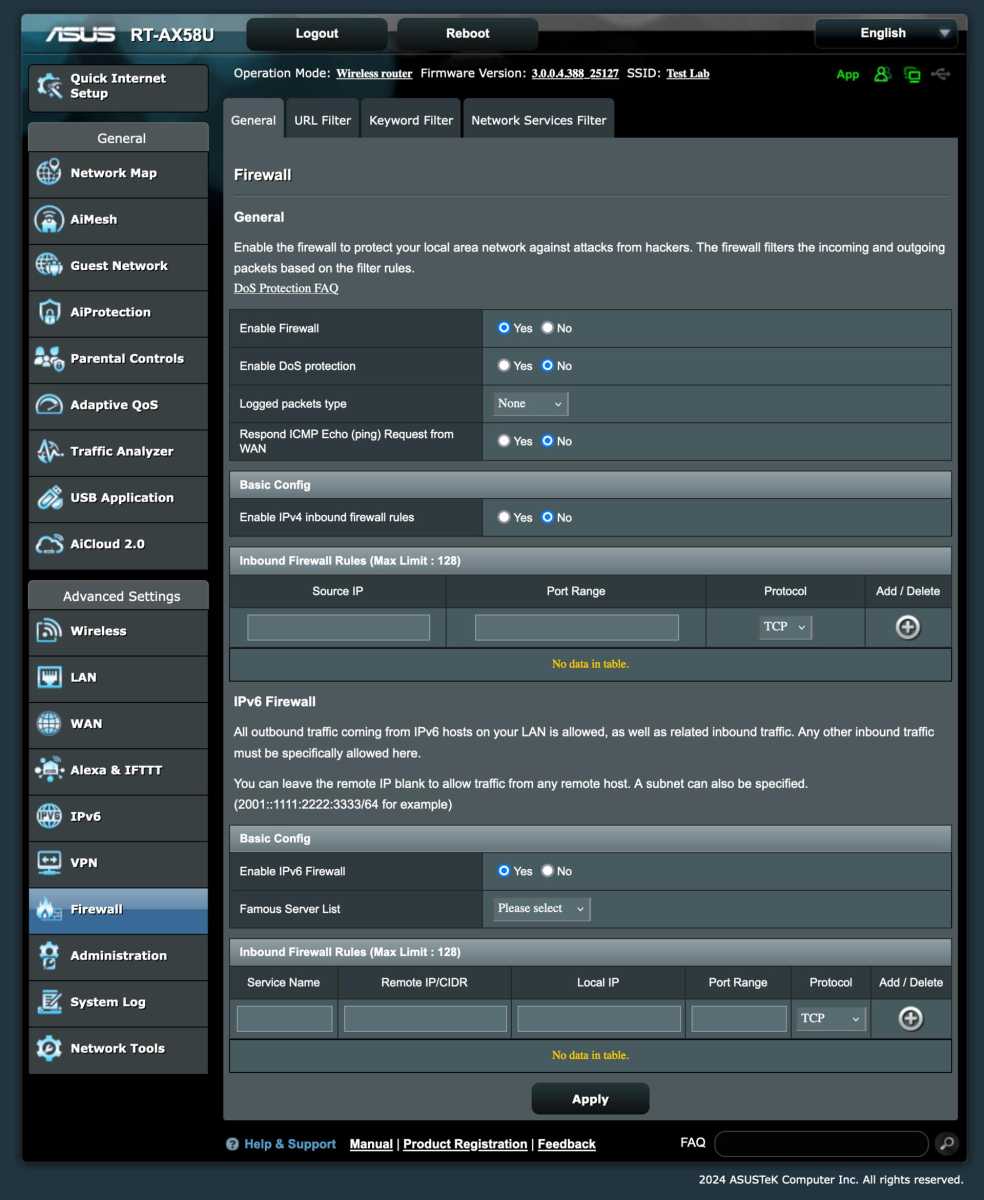
Switch on the firewall
Most routers have a built-in simple firewall. Check that it is switched on and enable it if it is not.
Switch off unnecessary features
Many routers come with a bunch of features that were once considered safe or needed for one reason or another, but are now unnecessary. Here are some features you should avoid.
Hidden SSID
Most routers have the ability to hide the Wi-Fi network, meaning it doesn’t show up as a possible network to connect to. The problem is that it is still very easy to find for those who really want to, and it only becomes more complicated for you and others who will use the network.
Upnp
Universal plug-and-play, or upnp, is an outdated technology for enabling access to network services from outside. It was not intended to be used to access things from the open internet, and it leaves your network vulnerable. Only switch it on if you later realize that something you really need requires the feature to be turned on.
Wps
Wi-Fi protected setup (aka wps) is also an outdated technology that was meant to make it easier to connect gadgets without a user interface, like printers, to the network. However, it has known security flaws and modern gadgets connect in other ways, such as with qr code.
MAC filter
All network devices have a hardware address, also known as a MAC address (not to be confused with Apple’s Mac computers). A MAC filter in the router means that devices whose MAC address you haven’t added won’t be allowed to connect. The only problem is that a hacker can easily clone one of your devices’ addresses to sneak past the filter, while making it much more complicated to connect new gadgets.
Remote logging
Some routers have a feature that allows you to log in and change settings by connecting from the internet to your home IP address. This is a bad idea and leaves you vulnerable.

Foundry
Use guest networks
Many routers have a handy feature that creates a separate wireless network, often called a guest network. Devices connected to the guest network have access to the internet but cannot access your computer and other devices on the regular network. They cannot normally connect to each other either, although some manufacturers break this rule.
Some routers allow you to create more than one guest network. You can use this to segment your network and protect your most important devices. For example, if you connect potentially insecure smart home products to a guest network, a hacked device will not give the hacker the opportunity to try to access your computer, mobile phone, or router.
More advanced routers and routers on which you install alternative software such as Open WRT, allow you to create other types of segmented networks using a technology called vlan. For example, you can create a network for smart home devices that cannot access the internet, and then provide sufficient access to and from the regular network to control the devices with, for example, the smart home platform Home Assistant. More on this in a later guide!
Foundry
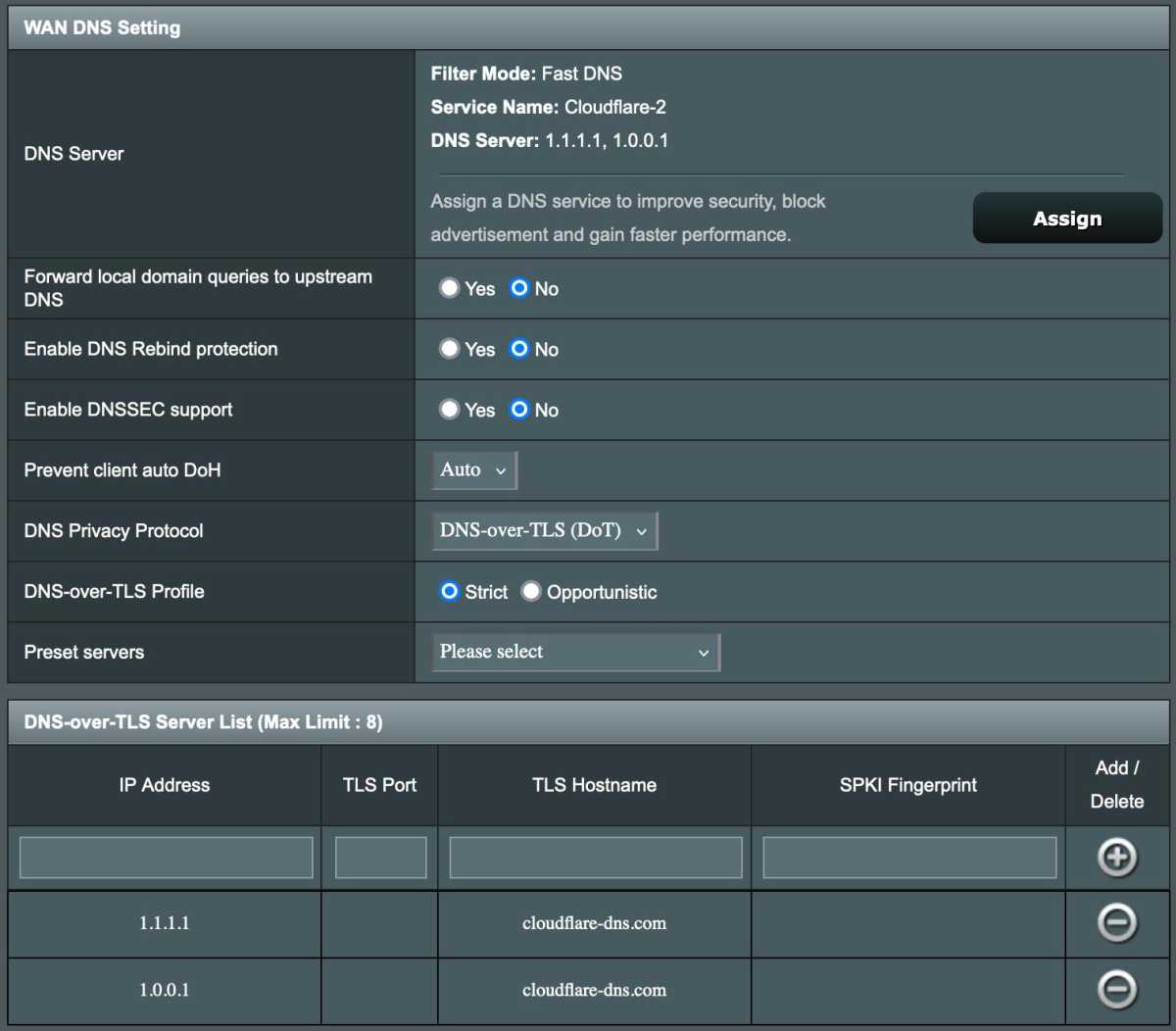
Encrypted dns for everyone on the network
Most traffic between browsers and websites today is encrypted, so that only you and each website you connect to know what you are communicating about. But some internet traffic is still transparent–domain name lookups.
For example, the DNS system translates www.pcforalla.se into an IP address. Your internet service provider has a DNS server to which the router normally forwards all domain name lookups. This means that the operator gets a lot of data about the websites you visit.
By using encrypted DNS, you can protect yourself from this monitoring. The settings can look a bit different, but what you’re looking for is something called dns-over-tls (dot) or dns-over-https (doh). There are several major operators of encrypted dns, Cloudflare being the best known.
Don’t forget to update
Routers are some of the most vulnerable devices on the internet, and hackers are constantly hunting for vulnerabilities to be able to take over routers en masse and allow them to be part of botnets.
If your router has a setting to automatically install firmware updates, I highly recommend turning it on. If not, you should set some kind of reminder to check for updates at least once a month.
It’s also important to keep your connected gadgets up to date. Computers, mobiles, and tablets are easy to remember and they often show notifications alerting you to updates, but don’t forget other gadgets such as printers, televisions, and various smart home products.
Fing
Keep track of connected gadgets
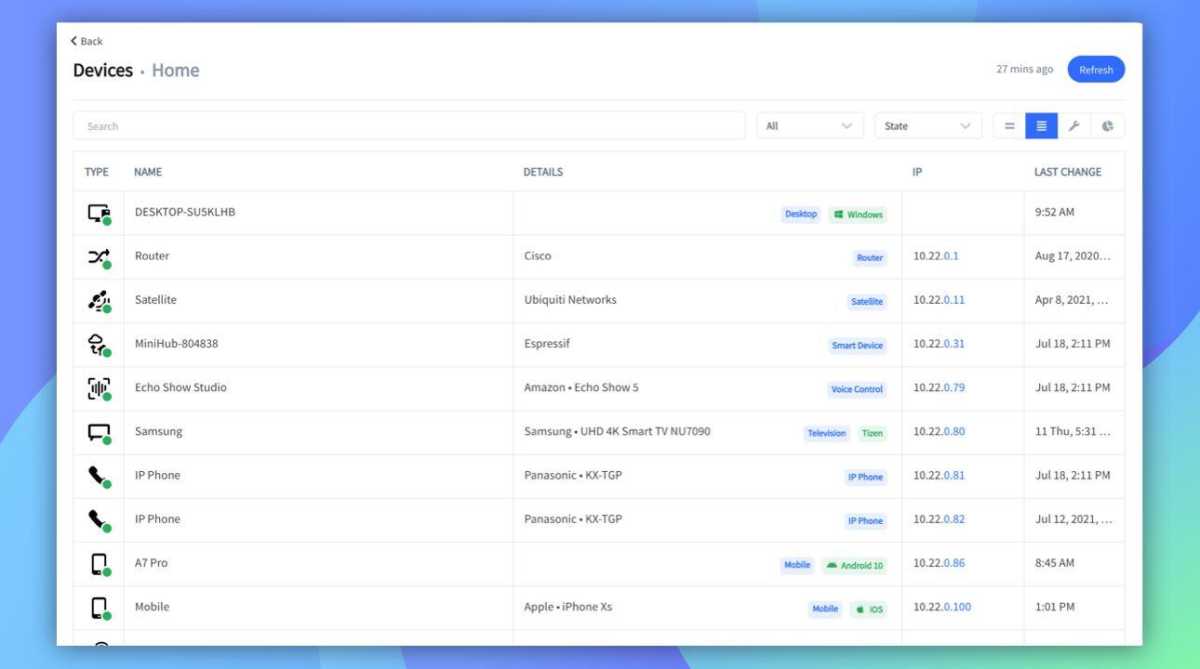
It can be a good idea to scan the network from time to time to see all connected devices. Even if you never detect any unauthorized devices, it can be useful, for example, by reminding you of gadgets you have that may need updating.
Some routers have a built-in feature that displays all connected devices by name, IP address, and MAC address. If your router doesn’t have this, you can use a program on your computer such as Fing.
Don’t be alarmed if you see devices that you don’t immediately recognize. Most connected gadgets choose strange device names. Fing can be a good choice here because the program can usually tell which manufacturer a device is from, making it easier to identify all devices.
Switch off your router when you’re away from home
If you’re going to be away from home for more than a few days, it’s a good idea to switch off your router. This prevents outsiders from trying to get in, and devices in your home from communicating with the internet unnecessarily.
An exception to this is if you have, for example, smart surveillance cameras that you want to be able to access from outside, or have a connected alarm of some kind (either for burglary or for water leaks, for example).
Switch on additional security features in the router
Many routers have additional security features that can help protect you and others connecting to that network. For example, Asus has features like AI Protect and Parental Control.
Such features can, for example, analyze network traffic and block connections to known malicious sites, or block parts of the internet for certain devices (children, for example). As there are many different features that look different from one manufacturer to another, I can’t go through what’s available and what’s worth enabling on your particular router, but go through your router’s settings carefully and search for more info on a feature if you’re curious.
Protecting your accounts for connected gadgets
Today, many connected devices in the home use manufacturer accounts for remote access, updates, and more. As long as these devices have access to the internet, these accounts pose a security risk. A hacker who gets into an account can spy on you–how much depends on the gadgets involved, the worst being connected cameras as the hacker can see (and record) everything that happens in front of the cameras.
It is possible to use such gadgets without the internet, for example by only using them via Homekit or Home Assistant and placing them on a separate network where the firewall blocks the internet. If you don’t have the time or inclination to get involved, it’s important that you protect these accounts as best you can. Choose secure, unique passwords, enable two-factor authentication, or switch to key logins.
Foundry
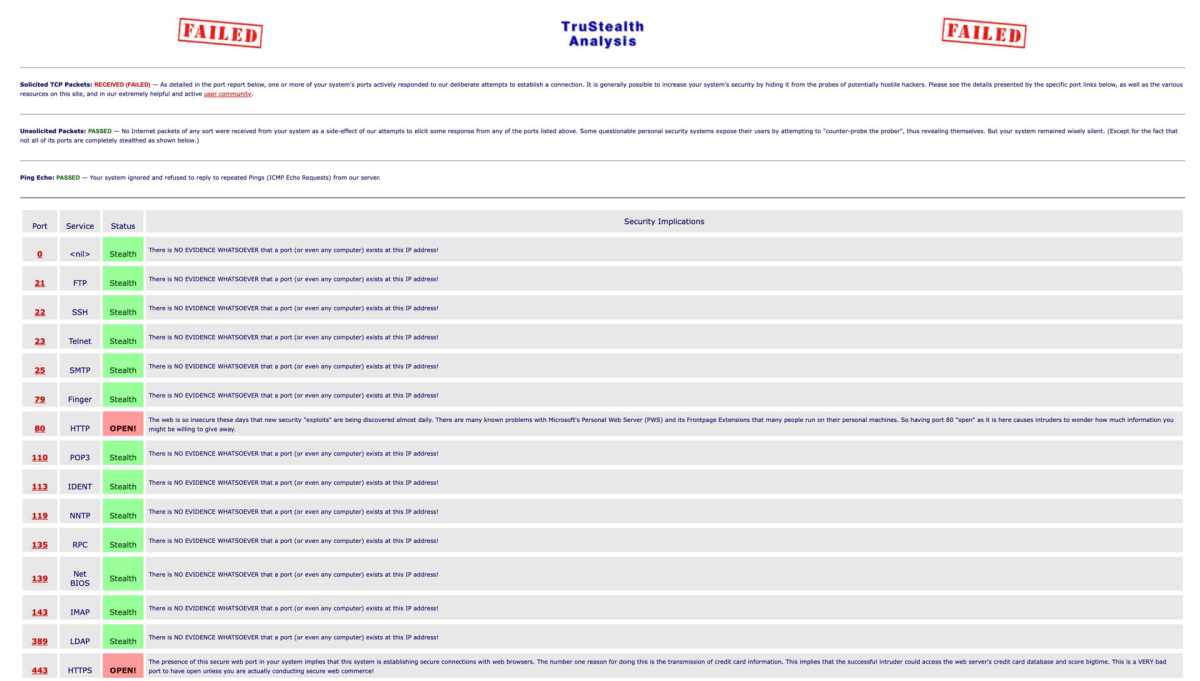
Don’t open ports to the outside world
In the past, it was common for applications to require others to contact them directly over the internet. For devices behind a router with address translation, this meant opening the router with port forwarding technology. This was the case for various file-sharing services, chat programs and games. For example, some Xbox games required port 3074 to be forwarded from the router to the game console. The website portforward.com lists thousands of games and programs and the ports they need.
Modern programs and games have almost completely switched to other network technologies and do not need any open ports. Check your router’s port forwarding settings and remove any forwarding you no longer need.
You can also test whether your router has any ports open to the outside world using, for example, Shields Up from renowned security researcher Steve Gibson. The site isn’t exactly intuitive, but click on “All Service Ports” at the bottom and it will check all the usual ports. A more advanced option is the nmap program, which you can use to scan your own router from the outside by first connecting to a VPN service.